A Review Towards the Development of Ontology Based Identity and Access Management Metamodel | SpringerLink

D4.7: Review and classification for a FIDIS identity management model: Future of IDentity in the Information Society
.fig.001.jpg)
Figure 1: The proposed model of the antecedents' Corporate Identity Management (CIM)., Corporate Identity Management (CIM) Model in Malaysian Higher Education Sector: Literature Review and Hypothesis Development
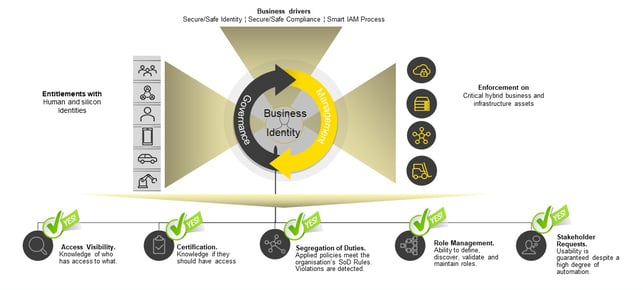
A modern and cloud-native approach for identity and access governance, data quality, and data accuracy.